Why Post-Quantum Cryptography Matters Now
News, insights and updates from the team at Bloom Equity Partners
Happy Friday technology investors, operators, and enthusiasts.
We’re here again with The Bi-Weekly Bloom – one of the best resources for Private Equity, Enterprise Software, and Technology news. In each edition, we delve into:
PE Interest in Technology
Our team’s favorite articles and podcasts from last week
Insightful tweets from fellow investors and operators
Join nearly 10,000 readers for a summary of our favorite software insights, articles, podcasts, tweets, and news headlines, subscribe below:
Why Post-Quantum Cryptography Matters Now
Both Gartner and Deloitte have identified Post-Quantum Cryptography (PQC) as a top technology trend for 2025, underscoring its urgency as quantum computing advances. While quantum technology promises breakthroughs in drug discovery, AI, and optimization, it also poses a major cybersecurity risk—one that could render today’s encryption methods obsolete as early as 2029.
For financial institutions, healthcare providers, and SaaS platforms, this presents an existential challenge: data secured today using traditional encryption methods could be harvested by cybercriminals and decrypted once quantum computers become powerful enough—a scenario known as "harvest now, decrypt later."
What is Post-Quantum Cryptography (PQC)?
Post-Quantum Cryptography or PQC is a new class of encryption algorithms resistant to quantum attacks. These algorithms rely on mathematical problems that even quantum computers cannot solve efficiently and secure against attacks from both classical and quantum, addressing potential vulnerabilities of current cryptographic systems to developments in quantum technologies. Unlike quantum cryptography, which uses quantum principles to transmit data securely, PQC is designed to replace classical encryption methods in everyday applications—from secure email and online banking to cloud storage and VPNs.
The Quantum Threat: Why Encryption is at Risk
Encryption methods like RSA, ECC (Elliptic Curve Cryptography), and Diffie-Hellman—which secure financial transactions, medical records, and corporate data—are based on mathematical problems that classical computers find difficult to solve. However, quantum algorithms like Shor’s Algorithm will be able to factor large prime numbers exponentially faster, breaking these encryption methods almost instantly.
🔹 Gartner estimates that quantum computing will break today's encryption by 2029, putting sensitive financial and healthcare data at risk. Currently, encryption methods like RSA (Rivest-Shamir-Adleman), ECC (Elliptic Curve Cryptography), and Diffie-Hellman are widely used to secure digital communications. These algorithms rely on the computational difficulty of factoring large prime numbers or solving discrete logarithms—tasks that classical computers find infeasible within a reasonable timeframe. However, quantum algorithms, notably Shor's algorithm, can efficiently solve these problems, rendering such encryption methods vulnerable
🔹 Deloitte highlights that major financial institutions are already transitioning to quantum-secure encryption, preparing for a future where standard cryptographic methods will be ineffective. The proactive shift among leading banks and cloud providers toward quantum-safe encryption underscores the industry's recognition of the impending threat.
🔹 Booz Allen warns that organizations without a transition plan could face catastrophic data breaches once quantum decryption capabilities emerge. The firm is a leading provider of cybersecurity services working on nearly 300 active cybersecurity projects and serving numerous government agencies focused on national security and data protection. Their analysis highlights the urgency for enterprises to assess cryptographic vulnerabilities and develop transition strategies before quantum threats become a reality.
The implications for businesses are clear: without quantum-resistant cryptography, organizations risk data exposure, financial losses, regulatory penalties, and reputational damage.
Challenges in Transitioning to PQC
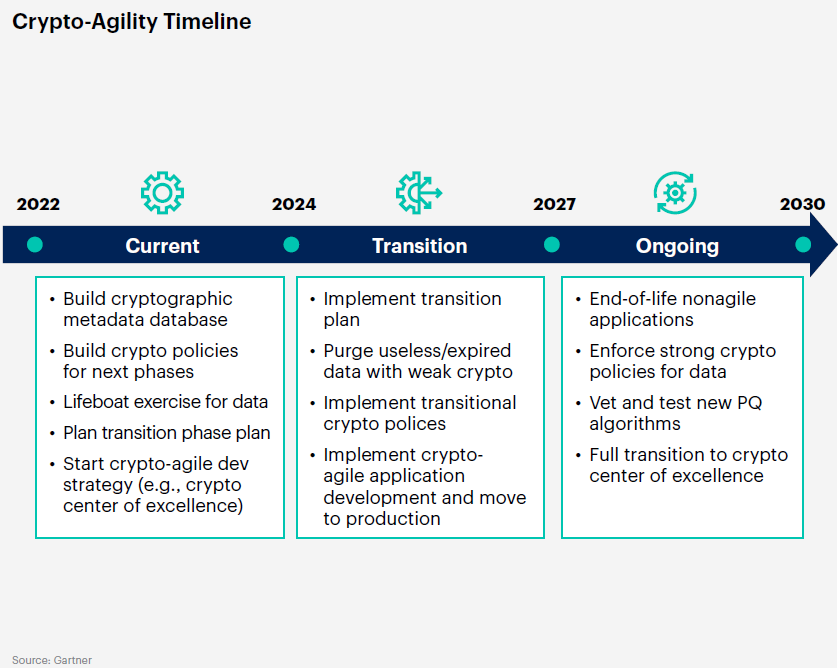
While adopting PQC is essential, transitioning away from legacy encryption is a complex, multi-year process.
🔹 Cryptographic Agility – Organizations must develop systems that can seamlessly switch between encryption methods without overhauling their entire infrastructure.
🔹 Backward Compatibility – Many systems still rely on 20+-year-old encryption standards. Transitioning to PQC requires careful integration with legacy systems to avoid operational disruptions.
🔹 Industry Standardization – The National Institute of Standards and Technology (NIST) is finalizing its PQC algorithm recommendations, but enterprises must start preparing now rather than wait for regulatory mandates.
🔹 Cost & Complexity – Transitioning large-scale enterprise systems to quantum-secure encryption requires significant investment in infrastructure, training, and cybersecurity strategy.
Despite these challenges, organizations cannot afford to delay. With a structured approach and proactive planning, the transition to quantum-resistant security is both feasible and essential.
The Path Forward: Preparing for a Post-Quantum World
While all industries will eventually need to adopt PQC, financial institutions, healthcare providers, SaaS platforms, and government agencies face the most immediate threats. These sectors store high-value, long-lifespan data that could be intercepted today and decrypted in the future. Several leading banks and cloud providers have already begun testing quantum-safe encryption, recognizing that waiting until quantum computers are fully operational will be too late.
Organizations must start preparing now to avoid falling behind. This begins with assessing current cryptographic systems, developing a PQC transition roadmap, and ensuring cryptographic agility—the ability to seamlessly switch between encryption methods. Companies should closely monitor NIST’s PQC standardization efforts, invest in quantum-secure encryption solutions, and partner with cybersecurity experts to future-proof their security infrastructure.
The shift to PQC will define the next era of digital security. Industry leaders aren't waiting for quantum computers to become a reality—they're acting now to protect their long-term data security. By evaluating cryptographic vulnerabilities, developing transition strategies, and embracing cryptographic agility, forward-thinking organizations are positioning themselves not just to mitigate quantum threats, but to lead confidently in the post-quantum landscape.
References:
Gartner: “2025 Top Strategic Technology Trends”
Deloitte: “Tech Trends 2025”
Booz | Allen | Hamilton: “Post-Quantum Cryptography, Explained”
About Bloom Equity Partners
We’re big fans of mission-critical enterprise software, technology and tech-enabled business service companies with a competitive moat and a loyal, diversified, and growing customer base. Whether the business is bootstrapped, VC-backed, or a division of a larger organization, Bloom is completely agnostic to the structure. We are actively seeking investment opportunities that fall within the criteria below. We welcome the opportunity to discuss potential investments with founders, operating executives and intermediaries.
Our Investment Criteria
Industry: B2B Software and Technology-Enabled Companies
Geography: North America, Europe, Australia and New Zealand
Revenue: $5M - $50M
Growth: No requirement
Profitability: Negative - $10M EBITDA
Investment Type: Operational control required
If you or someone you know is considering selling or investing in their business, we would love to learn more! Check out our referral partner program, which compensates referrers for introductions that lead to affirmative outcomes.
What We’re Reading and Listening To…
The Complete Guide to SaaS Pricing Strategy
Favorites from the Ecosystem
Investors…
Operators…
Founders…
If you’re enjoying The Bi-Weekly Bloom, we’d appreciate it if you shared it with your network.